Password Strength Meters - misleading sense of security
Passwords are the main weak link in the security chain between a user and any digital platform; they rely on the user supplying a secure, hard to guess and unique password, something many find difficult. Password managers can go a long way in helping solve this problem, but uptake amongst the general population is low.
The use of a strong, random and unique password can slow down various attack vector, but many users re-use passwords across their multiple accounts resulting in the possibility of a compromised account exposing their entire digital life. Let's avoid the topic of users and what they should do to protect their password, website owners can utilise a range of measures to help store a users password (hashing for example - don't store the password) or provide prompts to enforce a string password policy via a ‘password strength meter’. It is the latter I wanted to focus in this post.
Recently I was testing several online services, for which I have a ‘strong’ but repeatable password and a throw away email address, where the same password was receiving different ‘strength indicator’ outcomes. I decided to dig a little deep and explore this inconsistency and wonder if this inconsistency in itself is leading to complacency by users and making us more insecure.
While writing this post Troy Hunt posted about password strength meters and how they allow users to make ill-informed choices. My post in similar in tone and nature.
Just blogged: Password Strength Indicators Help People Make Ill-Informed Choices https://t.co/g3pFePUrBA
— Troy Hunt (@troyhunt) July 5, 2017
The Password
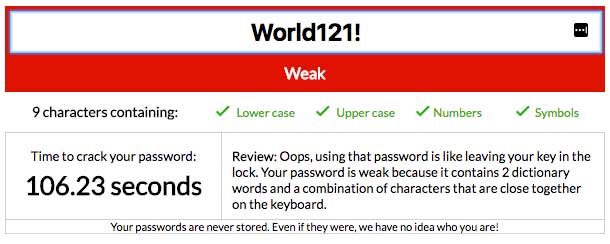
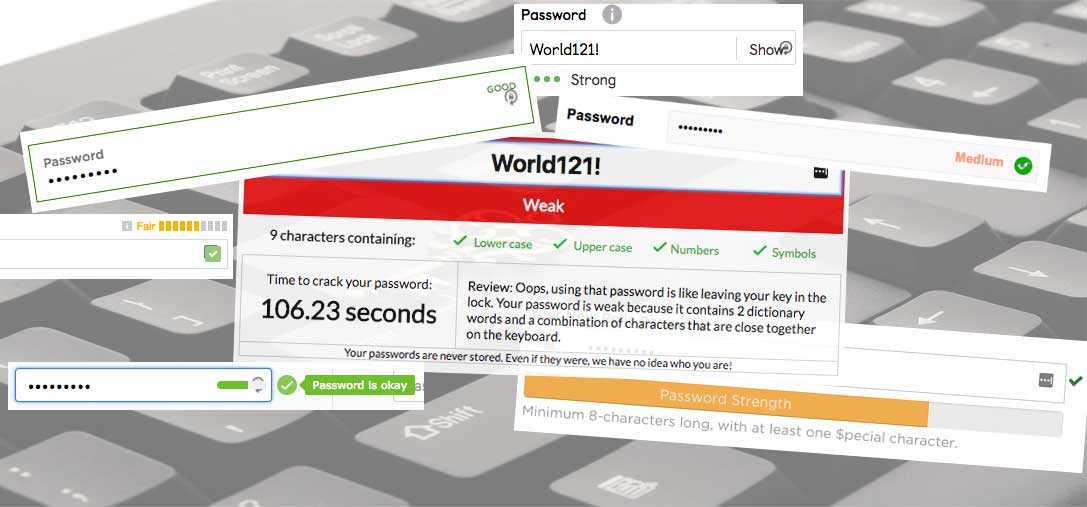
Let's take the password 'World121!', it is not unique, it uses common characters and is present in every password directory I could find. Equally, due to its simplicity it would be very easy to 'crack' and decrypt (if it is encrypted at first). Using the example password cracker above, the password has been identified as weak, but this is a little misleading, what is meant by 'weak'?
Same password - different outcome
Let's see how this password fairs on some popular sites that use a password manager.

The Daily Mail have a bizarre password policy that does not make much sense, I sent them a tweet, for which they gave no response.
Hey @MailOnline why ask me to provide a strong password then place an arbitrary limit of 15? pic.twitter.com/9erWiZuLWT
— Dan Leightley (@_Dr_Daniel) July 8, 2017
They suggest that my password is 'Medium', but what does this mean? Medium out of what? And it is also client side scripting which is a simple regex detection of certain key words.
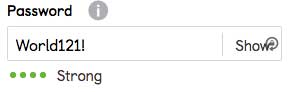
Now on to GumTree, they are suggesting that my password is 'Strong'. Great, but what does this mean?
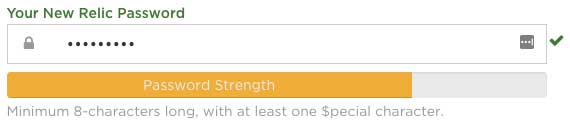
Then I moved on to a site I use often, New Relic, they have a strength meter with a orange bar, I am close to the end of the bar... does this mean the password is good? I have no idea.
How about Reddit? They suggest my password is 'okay', okay against what? I have no reference point! This is starting to get a little confusing with all the password strength terminology.

Let's take a look at Virgin American, again, what does 'good' mean?

Let's go take a look at Twitch, now they've thrown a new word into the mix - 'fair' - what is a fair password?
The examples above show password strength meters based on simple in-browser calculations with terminology that is misleading. Password strength meters provide a misleading sense of security and lead the user to create insecure passwords. It is difficult to determine what is a "good" or "bad" password strength meter, many have been coded with the website own password policy. Maybe a standard needs to be defined here?