Trusting basic https security in health-related smartphone apps
Almost everyone has a smartphone, it is the primary means connection to the world around us. Over the last few years we have seen an exponential increase in the development and release of smartphone apps, but what many users do not realise is the type of information they collect and the way they share that information.
Think about your health - it is highly sensitive and personal - do you want this information shared openly for anyone to see? No, of course not! But how do you know it is being sent securely? With a prefera of health apps out there, is there any way to check how secure they are?
Users have become conditioned to the padlock in their browser, this website uses https, but when it comes to a smartphone app they have no visual way of knowing how secure their data is. Ask any user "is your data secure when being sent from an app" they will answer "I do not know" or "I hope so".
Smartphone app security is an important consideration, their are many attack vectors where malicious persons can intercept insecure traffic, read and modify it before it is then sent on. A basic way to combat this is the use of https (Transport Layer Security - TLS), which encrypts the data between the sender and receiver. It is free, simple and easy to deploy so there is not really any excuse anymore.
Introduction
In this blog post I wanted to demonstrate the type of security used by some popular smartphone apps; and why, as a user, we should not necessarily trust them to protect our data. I decided to setup a simple local network at home, anyone can do this with ease. The objective was to see how easy it is to intercept data sent from an app.
To achieve this, I setup my own hotspot network using my Macbook Pro (ethernet) and used WireShark to monitor traffic between my Android device and the app servers. There are more sophisticated methods, however this is not the point of this article - simple and basic approach - to show how anyone can intercept traffic on a network.
I decided to take a look at some of the apps available in the Google Play Store Health section on how secure the data being sent is, and what is being sent. Here are some examples of the issues I found, it is important to note that this is a selection of popular apps from small number of downloads (1,000) to high (5 million) there were many more with issues - some I will follow up in later blog posts.
Olumia Life
You can find Olumia Life in the Google Play Store here. Olumia markets itself as a personal trainer, nutritionist and sleep specialist all wrapped into a single app. The stats suggest the app has between 10,000 - 50,000 downloads.

If you head over to their site, it has https, which is great start, you hope it would be the same for the app - but it turns out that the app does not using https and sends all its data insecurely!
Looking at the app further, you have to "Register an Account" to gain access; all seemed fine from a user perspective until you check out what data was sent and the method.
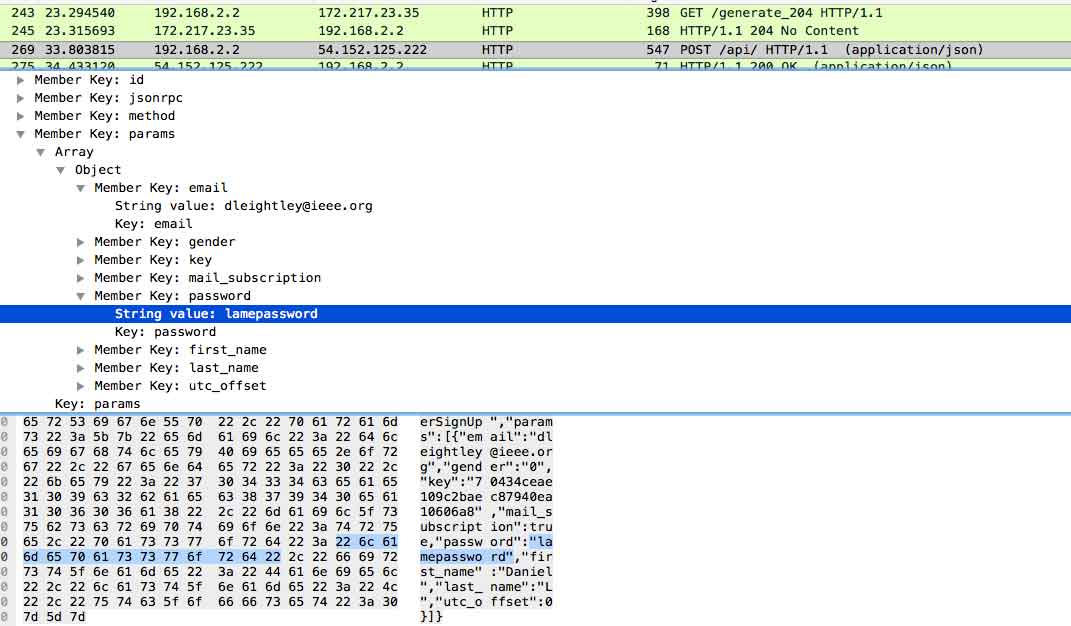
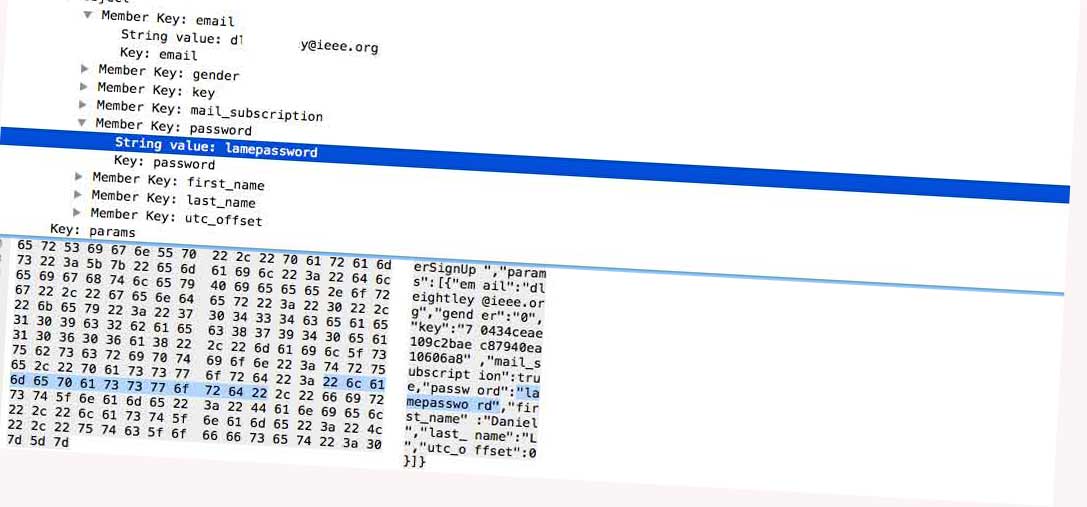
Look at that, my lame password and email are being sent over an insecure connection for anyone sniffing my wifi to obtain. But it was not just my password/email being sent insecurely, take a look at all this data being sent.
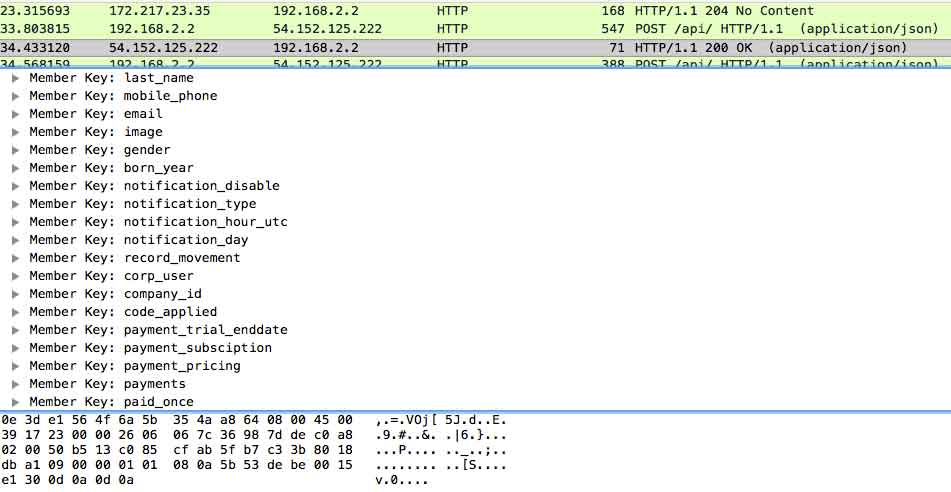
They have a variable for payment data, I did not perform any tests to see if payment details are sent insecurely, but that sure is a lot of information to be sent over an insecure connection. Typically you would expect this information to be separated between different API-end points.
So ultimately we have an app that is sending personal data related to fitness, nutrition and sleep insecurely. I have had no response from Olumia Life to my concerns via email, support ticket or Twitter.
What's Up
You can find What's Up in the Google Play Store here. What's Up? markets itself as a free app using Cognitive Behavioural Therapy and Acceptance Commitment Therapy to help users cope with Depression, Anxiety, Anger and Stress! The stats suggest the app has between 100,000 - 500,000 downloads.

The What's Up app is an interesting one, again it does not use a secure connection to transmit any data but does employ some encryption; the password is encrypted prior to transmitting the data.
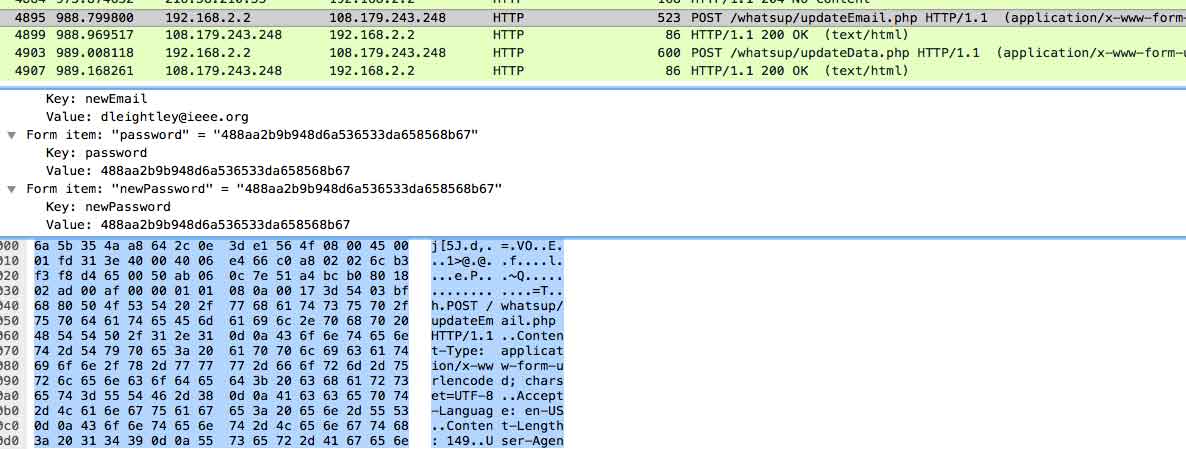
The password has been encrypted but it does not take much to decompile the app to identify the method used. Again, all data collected by the app is being sent over an insecure connection. When you attempt to post in the forum the username and password is once again supplied, suggesting the app stores the information locally; which is very bad practise. I contacted the developer who stated they plan on fixing these issues in a future update.
Westfield Health Claims
You can find Westfield Health Claims in the Google Play Store here. This app allows customers to claim for optical, dental, chiropody and therapy treatments via the app. The stats suggest the app has between 1,000 - 5,000 downloads.
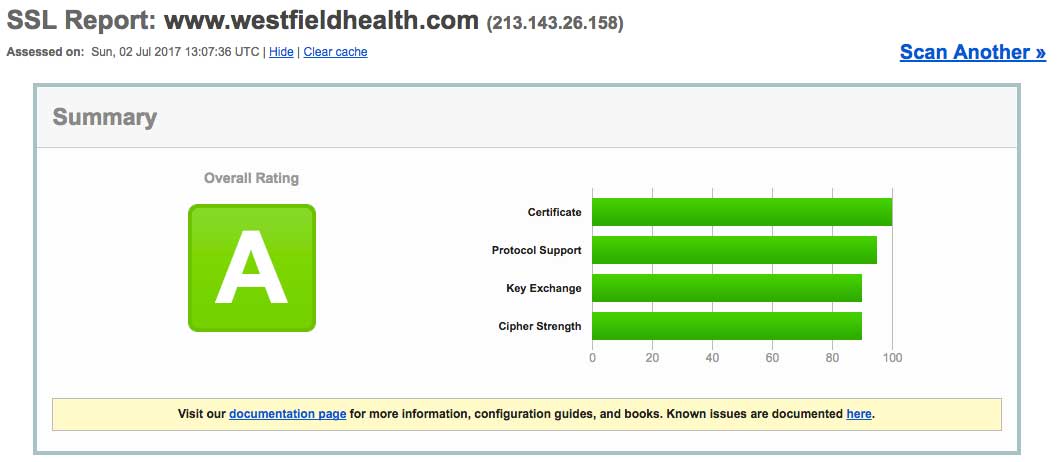
Before we get onto the app, take a look at Westfield Health Claims website, it uses https, which is great! They even get an overall A rating on SSL Labs.
Now heading to the app, you are unable to signup for an account, only login to a pre-existing account. For a new users you are redirected to the website to supply your details.

So we can only log in, we know that the website is secure but is the app? Answer, no, it shares your email and password via an insecure connection.
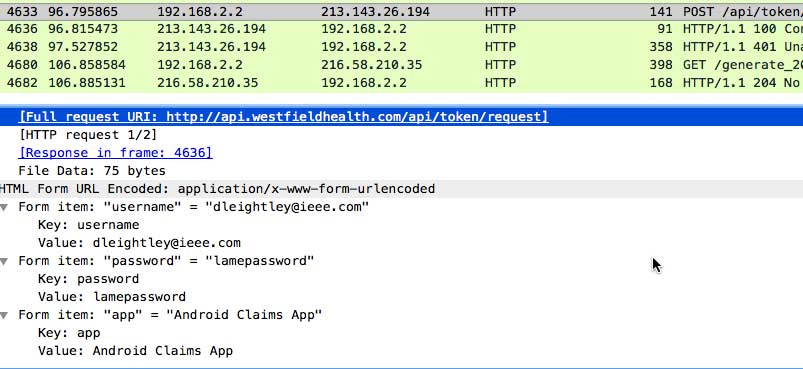
That unwinds all the hard work done securing the website. As I do not have an account with Westfield, I was not able to check the type of data sent by the app. The guys at Westfield Health were great, they sorted the issue out in less than 24 hour.
One You Easy Meals
You can find One You Easy Meals in the Google Play Store here. The app is designed to allow users to eat healthily by providing a range of recipes. The stats suggest the app has between 100,000 - 500,000 downloads.

The app it very basic, it enables users to join by providing first name, last name, email and postcode. I certainly would class these as personal identifiers and would have wanted them treating accordingly.
This is again sent over an insecure connection exposing the users details, OK, there is no password but other personally identifiable data points are present.
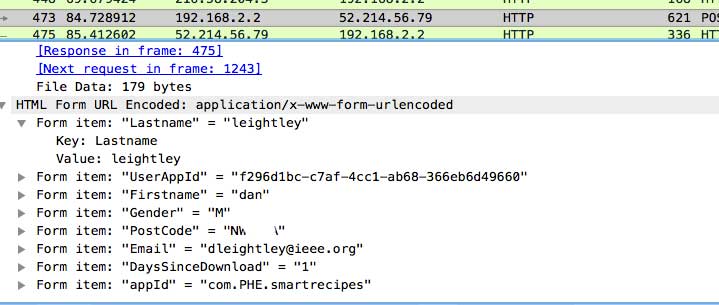
You could easily find my address, or start to build up a profile about me as an individual. I found it difficult to raise the issue, but it appears it got to the right people in the end as they fixed it.
Think Dirty
You can find Think Dirty in the Google Play Store here. The app is designed to allow users detect potentially toxic ingredients in your cosmetics and personal care products. The stats suggest the app has between 100,000 - 500,000 downloads.
Think Dirty, as with all the apps covered in this article, it again sends all its data via an insecure connection. But it goes one step further in how it shares this information, in one of the worst methods possible.
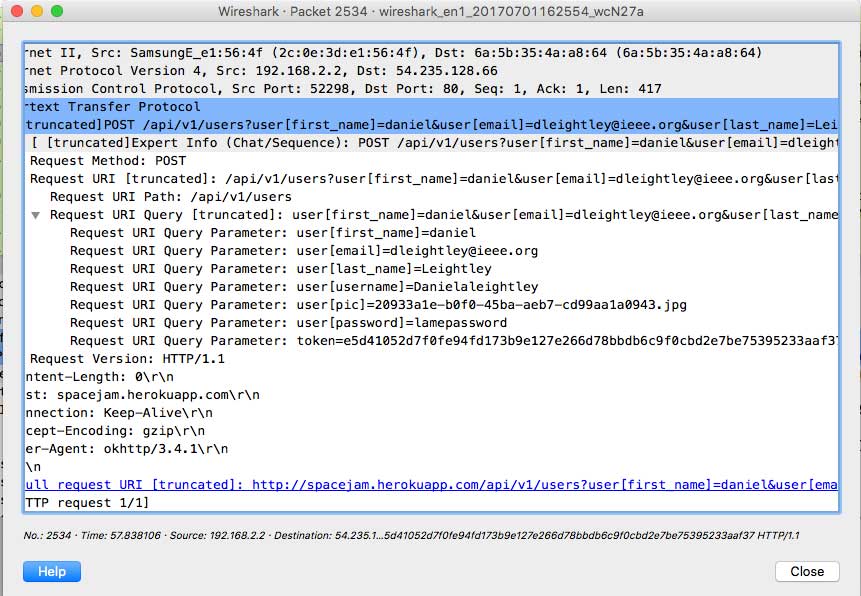
But what is of great concern is that my details are being sent as part of the POST request instead of it being attached to the request. This means that my username, password and email will be stored in the logs kept by my wifi routers, ISP and government agencies simply from the URL! This is bad. All data collected via the app (including barcodes scanned) are sent insecurely. I have had no response to my concerns from the Think Dirty.
Conclusion
This is just a flavour of what I found. There are other issues with these apps but i just wanted to focus on the connection and data sent over insecure connection. It is concerning that the developers have failed to implement basic security measures for apps that are being deployed in a sensitive domain, health. The information collected could exposure other online accounts, enable social engineering and expose sensitive information about the individual.